Penetration testing for developers
Nic Wortel
@nicwortel
About me
- Software Consultant & Trainer
- PHP, Symfony, Architecture, Docker, K8s, CI/CD
- Co-organiser at PHPAmersfoort
- Squad Leader / Instructor (reservist) at Royal NL Army
Why this talk?
Goals of this talk
- Improve security awareness
- Know some of the tools used to attack applications
- Test your own application using these tools

What is penetration testing?
A penetration test (or pentest) is an authorized simulated cyberattack performed on a computer system to evaluate its security.
Finding hidden files and directories
Google Dorks
Google search operators
| site:example.com | Search in specific site |
|---|---|
| filetype:pdf or ext:pdf | Search for specific file types |
| intitle:foo | Search in title tag |
| inurl:bar | Search in URL |
| intext:bar | Search in page content |
| -foobar | Exclude from results |
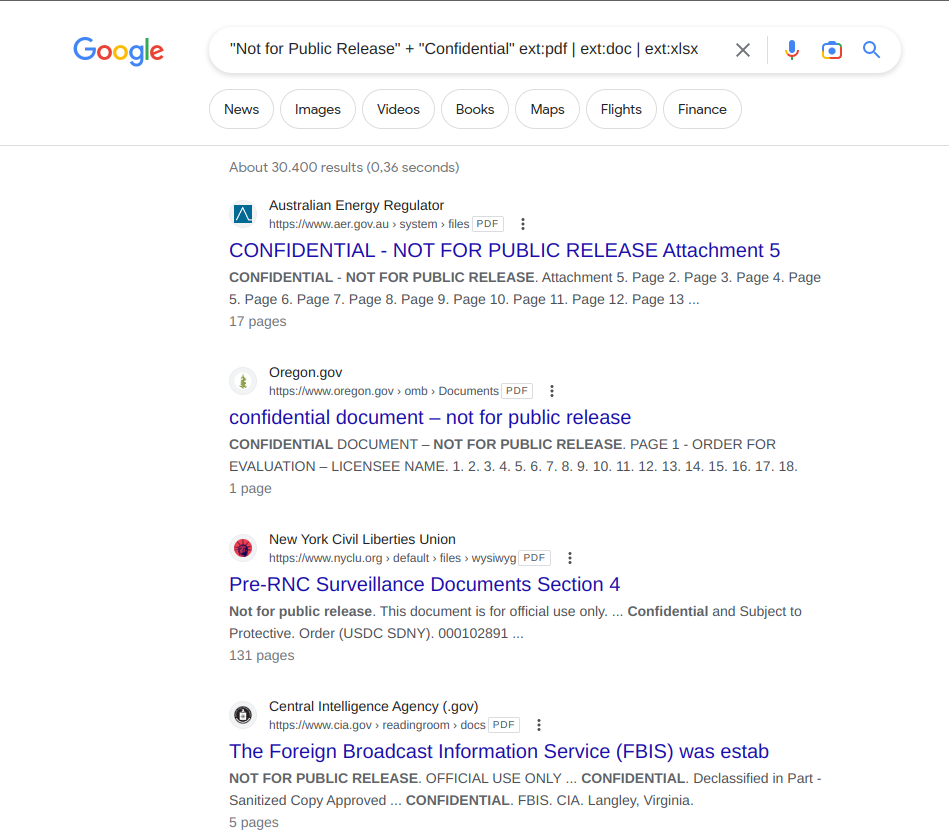
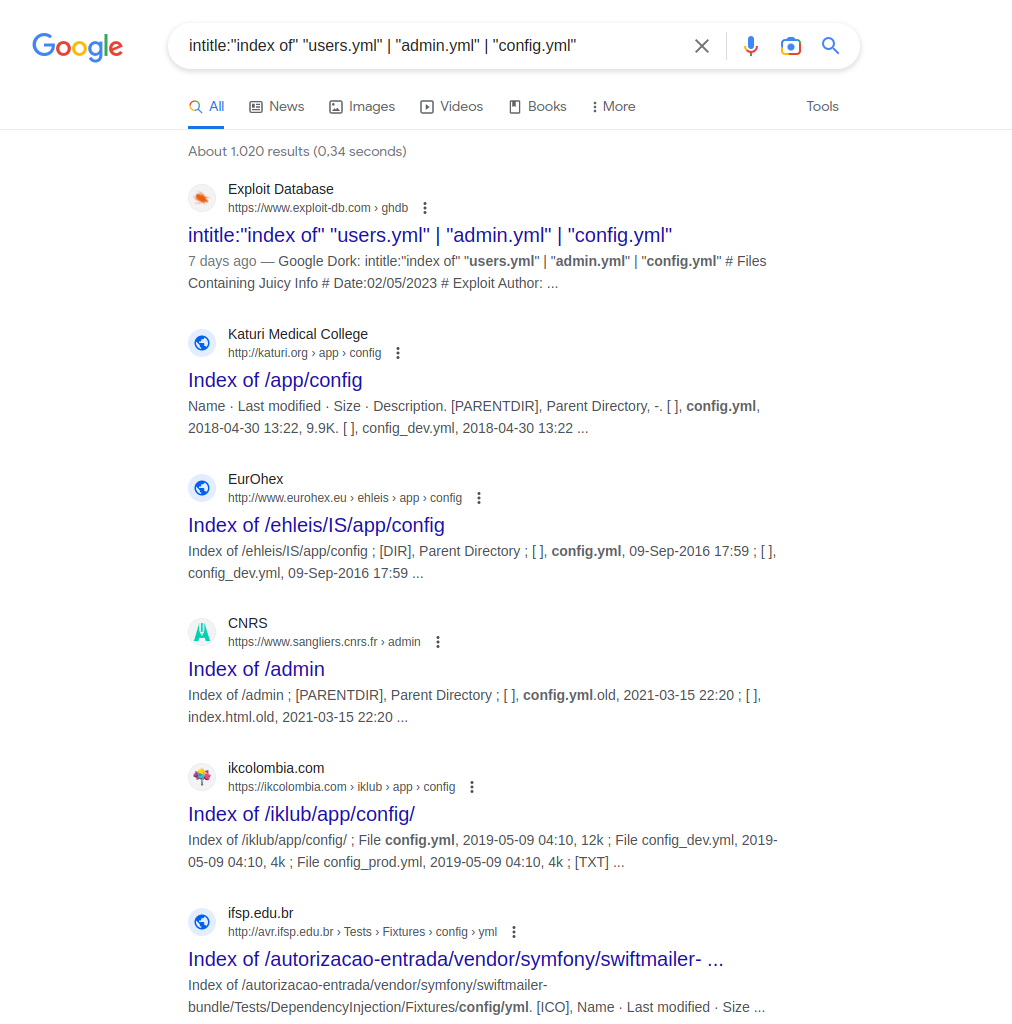
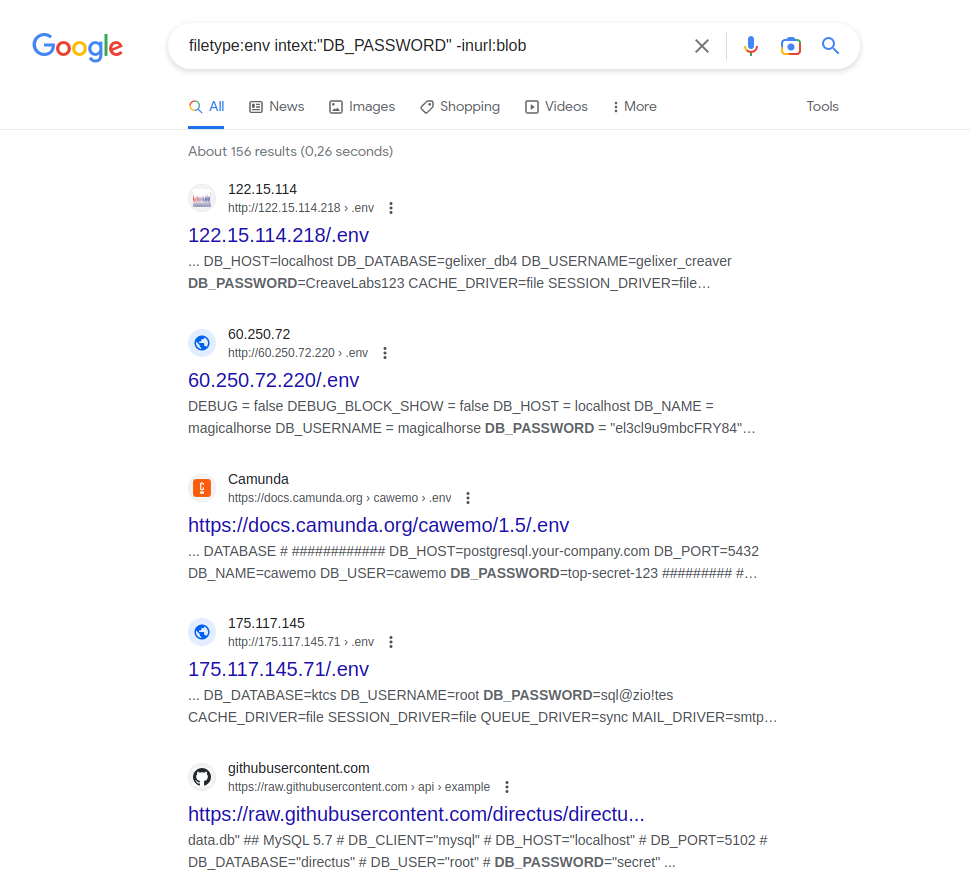
Google Hacking Database (GHDB)
https://www.exploit-db.com/google-hacking-database
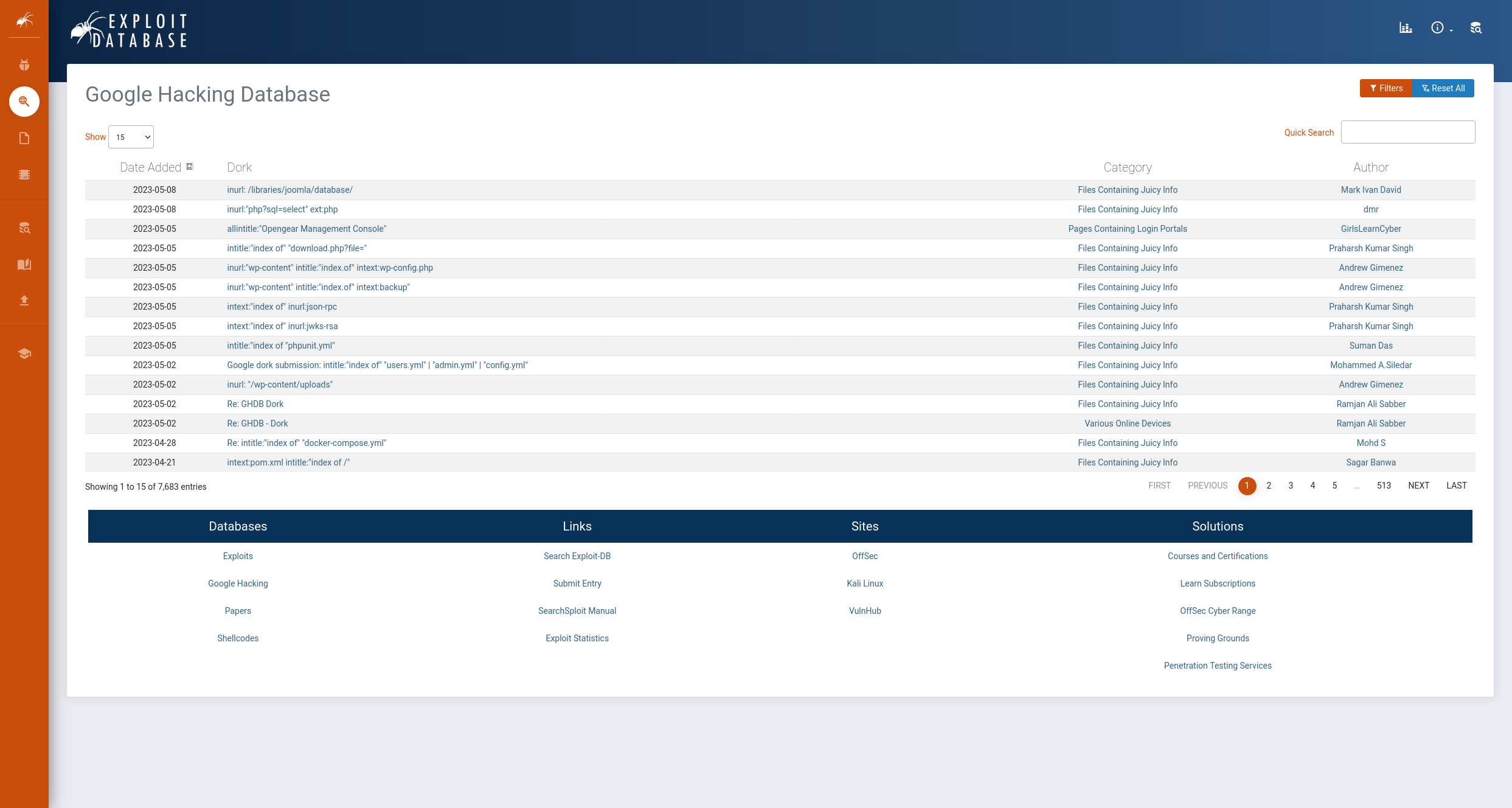
Focusing on a specific application
DIRB
Command line tool to look for (hidden) web pages and directories.
Wordlists
List of common filenames, passwords, usernames, etc. to use in dictionary attacks.

Lessons learned
- Don't be low-hanging fruit
- Keep sensitive files out of the web root
- Disable directory listing
- Enforce authorization for sensitive documents
Login brute forcing
Brute force attacks
aaa
aab
aac
aad
etc.
Dictionary attacks
123456
password
qwerty
iloveyou
etc.
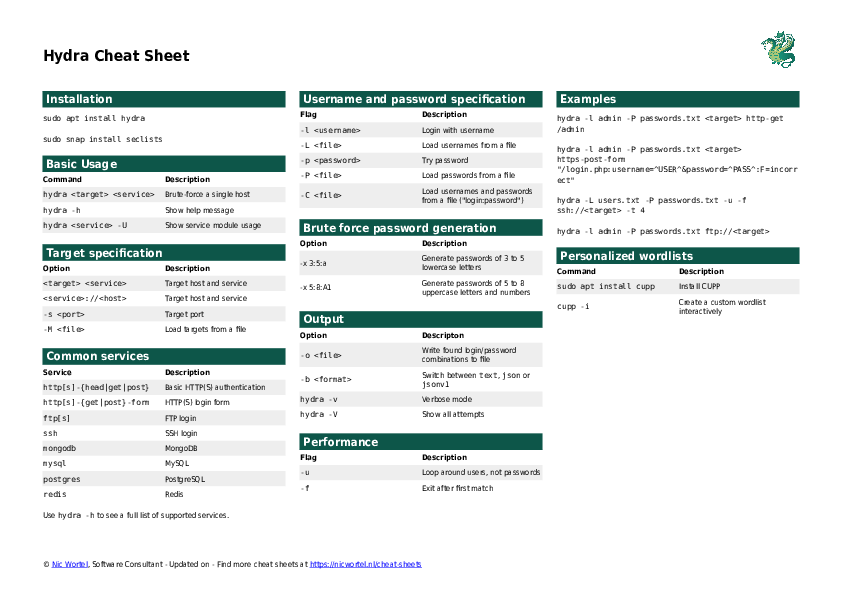
hydra
- Supports brute force as well as dictionary attacks
- Has modules to support various databases, services and systems
http-post-form module
"/login.php:username=^USER^&password=^PASS^:Incorrect username"

Lessons learned
- Block previously leaked passwords (Have I Been Pwned API)
- Implement 2FA
- Log authentication attempts / failures
- Rate limit failed login attempts
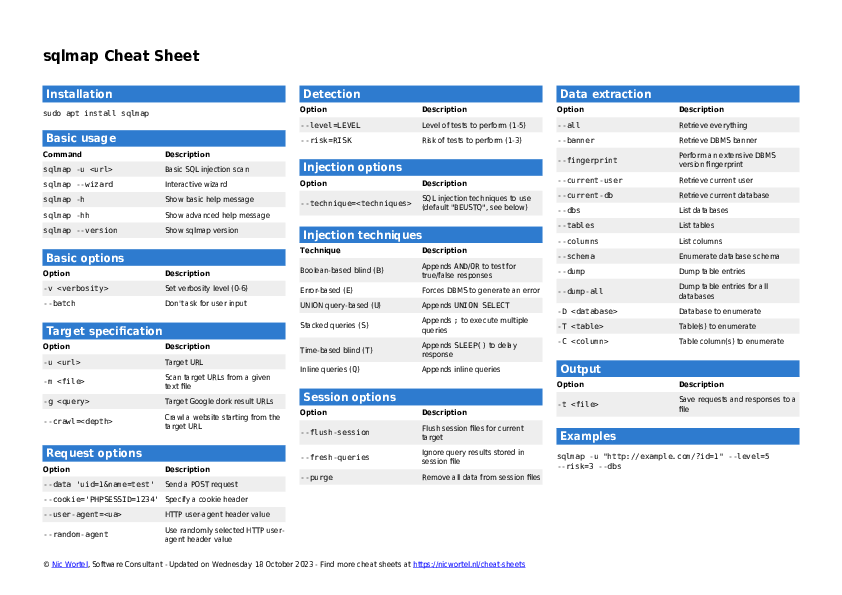
SQL injection
https://example.com/dogs?id=1
SELECT * FROM dog WHERE id = 1
SQL injection techniques
Error-based SQL injection
GTID_SUBSET(@@version,0)
SELECT * FROM dog WHERE id = GTID_SUBSET(@@version,0)
Error message:
General error: 1772 Malformed GTID set specification '8.1.0'.
UNION query-based SQL injection
1 UNION ALL SELECT 1,@@version,3
SELECT * FROM dog WHERE id = 1 UNION ALL SELECT 1,@@version,3
Stacked queries SQL injection
1; DROP TABLE dog
SELECT * FROM dog WHERE id = 1; DROP TABLE dog
Boolean-based blind SQL injection
1 AND (SELECT COUNT(*) FROM user WHERE username = 'admin' > 0)
SELECT * FROM dog WHERE id = 1 AND (SELECT COUNT(*) FROM user
WHERE username = 'admin' > 0)
Time-based blind SQL injection
IF(SELECT COUNT(*) FROM user WHERE username = 'admin' > 0,
SLEEP(5),0)
SELECT * FROM dog WHERE id = 1 AND IF(SELECT COUNT(*) FROM user
WHERE username = 'admin' > 0,SLEEP(5),0)
sqlmap


Lessons learned
- Use parameterized queries
- Turn off detailed error messages
- Use strong password hashing algorithms and salted passwords
Recap
- Google Dorks
- Web scanning with dirb
- Login brute forcing with Hydra
- SQL injection with sqlmap
Tools
Other tools worth mentioning
- Hashcat
- nmap
Operating Systems
Further resources
Cheat sheets
HTB Academy
Referral link for free credits