Finding security vulnerabilities with static analysis
- Nic Wortel
PHP & DevOps Consultant
About me
Nic Wortel



- PHP & DevOps consultant
- Organizer of PHPAmersfoort
- Instructor (reservist) at NL Army
Security risks for PHP applications
Could I be at risk?
Story
Finding a vulnerability in my first week on the project
Prevalence
82% of applications I audited contained security vulnerabilities
Source: own data
Business risks
Impact of security vulnerabilities
- Reputation damage
- Operational disruption
- Loss of revenue
- Fines
Targeted vs. untargeted attacks
The majority of cyberattacks are untargeted
You do not have to be a high-profile target to become a victim.
Impact of AI
Impact of AI generated code
Use of AI tools
92% of developers are using AI tools to generate code
According to a GitHub survey in 2023
https://github.blog/news-insights/research/survey-reveals-ais-impact-on-the-developer-experience/
Security of AI-generated code
30% of code samples generated by GitHub Copilot contained vulnerabilities
According to a study in 2024
Takeaway #1
Your PHP application could be at risk
Static analysis
Detecting issues in the code automatically
What is it?
The automated analysis of source code without executing it
Why use it?
Common use cases
- Detecting type errors
- Detecting potential bugs
- Detecting code quality issues
- Enforcing coding standards
- Automated refactoring
Popular tools
Commonly used PHP static analysis tools
- PHPStan
- Psalm
- PHP Mess Detector
- PHP_CodeSniffer
- PHP Coding Standards Fixer
- Deptrac
- Rector
Comparing to manual code review and automated testing
Benefits of static analysis
- Fast feedback
- Consistent results
- Does not require writing tests
- Covers entire codebase
Static analysis for security
Static application security testing (SAST)
Takeaway #2
Static analysis can help find security vulnerabilities quickly
Let's see what tools we can use
Code quality
Reduce the risk of introducing security vulnerabilities
Impact of code quality
Bad code quality makes it harder to spot security vulnerabilities
Prevalence
All audited applications had code quality issues
Such as:
- Code duplication
- Commented out code
- Error suppression / empty catch blocks
- High complexity
- Unresolved TODO comments
Checking code quality
Use common PHP tools to detect code quality issues
- Code complexity: PHP Mess Detector
- Code duplication: PHP Copy/Paste Detector
- Commented out code, empty catch statements, etc: PHP CodeSniffer
- Dead code: PHPStan / Psalm
Takeaway #3
Use code quality tools to reduce the risk of security vulnerabilities
Vulnerable dependencies
Libraries, frameworks, OS packages, PHP itself, etc.
Prevalence in audited applications
73% of applications used Composer packages with known vulnerabilities
Unknown vulnerabilities
55% of applications used unmaintained or abandoned Composer packages
Outdated PHP versions
15% of PHP installations no longer receive security updates
Source: Packagist.org package installations by PHP < 8.1 in February 2025
Unpatched PHP vulnerabilities
Unpatched PHP vulnerabilities
| PHP version | Known vulnerabilities |
|---|---|
| 8.0.30 | 1 |
| 7.4.33 | 2 |
| 7.3.33 | 6 |
| 7.0.33 | 21 |
| 5.6.40 | 13 |
| 5.5.38 | 74 |
Detecting vulnerable dependencies
Composer Audit

- Reports known vulnerabilities in Composer dependencies
- Uses Packagist's security advisories API
- Also reports packages marked as abandoned
Alternatives
External security monitoring services
- Private Packagist
- GitHub Dependabot
Scanning Docker images
Trivy / Snyk
- Scans a local directory or a Docker image
- Supports multiple package managers, including Composer
- Can report vulnerabilities in OS packages in Docker images
Takeaway #4
Regularly scan for vulnerable, unmaintained and outdated dependencies
To make sure your dependencies don't contain (known) security vulnerabilities
Committed secrets
API keys, private keys, etc. committed to version control
Detecting committed secrets
Secret scanning
- Trivy
- Snyk
- GitHub secret scanning
- GitLab secret detection
Security Misconfiguration
Insecure PHP configurations, Dockerfiles, etc.
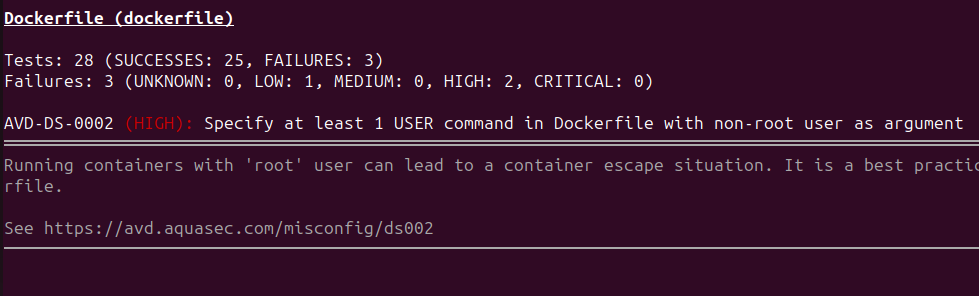
Dockerfile best practices
89% of Dockerfiles did not follow security best practices
Checking Dockerfiles for best practices
Trivy
Scanning php.ini configuration values
Iniscan
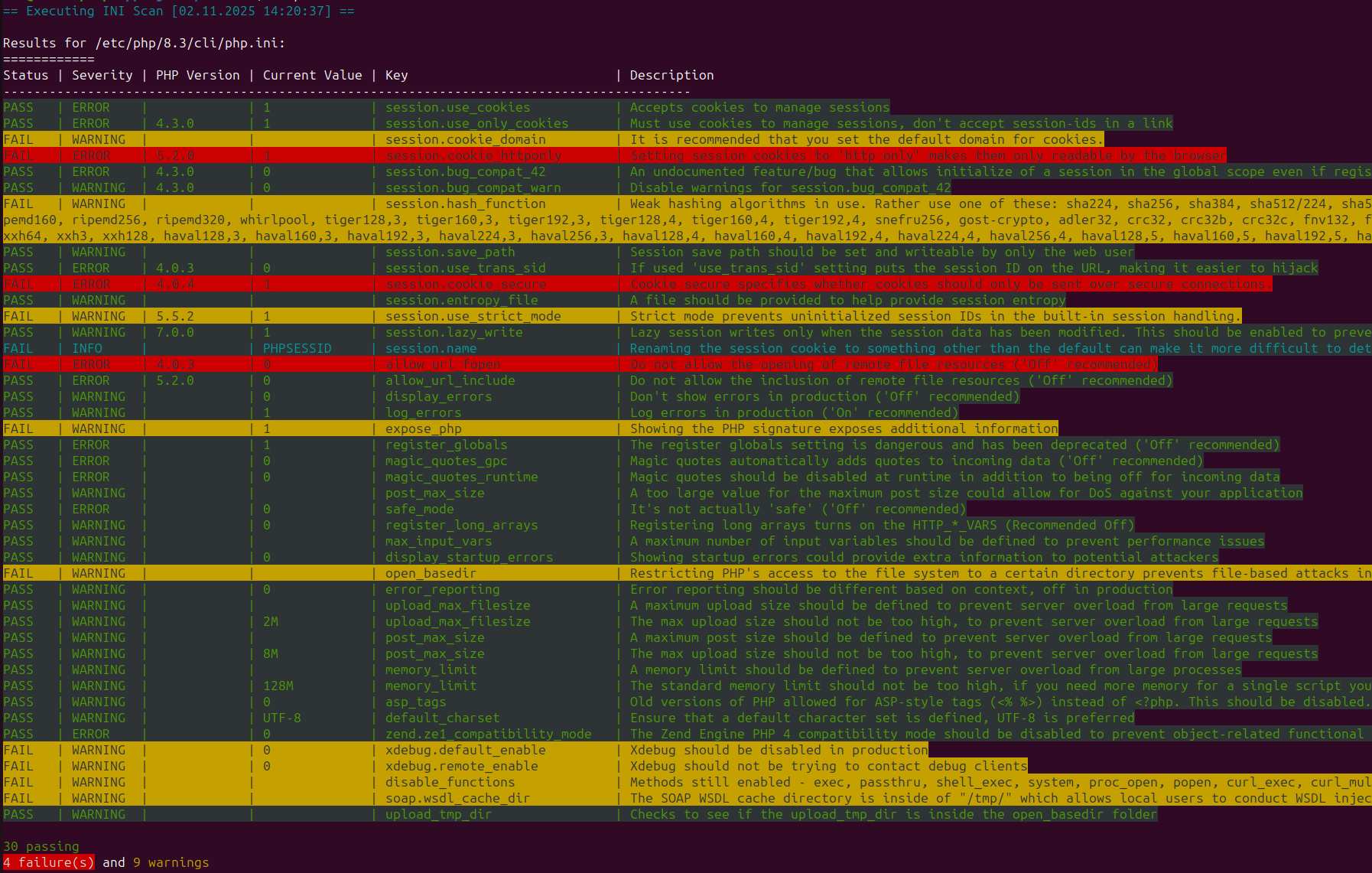
Scans your PHP environment for secure settings
- Secure cookie settings
- Not exposing the PHP version
- Restricting the files PHP can access
Using untrusted user input
XSS, OS Command Injection, SQL Injection, PHP Remote File Inclusion, SSRF, etc.
Injection-style vulnerabilities
In 18% of applications user input ended up in unsafe locations
- Cross-site scripting (XSS)
- Header injection
- Deserialization of untrusted data
- Unauthorized deletion of files
- Server-side request forgery (SSRF)
Taint Analysis
Detecting user-provided data that is used in unsafe ways
- Taint sources
- $_GET, $_POST, etc.
- Taint sinks
- SQL queries
- HTML output
- shell commands
- eval()
- etc.
Tools
Taint analysis tools
- Semgrep (freemium, multi-language)
- Psalm (open-source, PHP)
Comparison
Semgrep
- Supports various languages, including PHP
- Open source version only supports basic rules within single files
- Pro version supports cross-file analysis
- Has additional rules for other vulnerabilities
Comparison
Psalm taint analysis
- A separate analysis mode in Psalm
- Supports PHP only
- Supports complex analysis across multiple files
- Plugins improve support for popular frameworks and libraries (Symfony, Laravel, Doctrine, etc.)
Takeaway #5
Use taint analysis to detect injection vulnerabilities
Implementation in your development process
How to get started
One-time analysis
Run tools manually to analyse your project and see what they find
CI/CD pipeline
Run static analysis tools automatically for every commit
Scheduled
Find new vulnerabilities in dependencies for projects that are not actively developed
Not a silver bullet
Don't rely on static analysis alone
- Use automated tests
- Use manual code reviews
- Do an external security audit
Takeaway #6
Implement static analysis in your development process
Detect security vulnerabilities before they reach production
Wrapping up
- Your application could be at risk
- Static analysis: fast and consistent
- Code quality reduces security risks
- Monitor for vulnerable dependencies
- Use taint analysis
- Implement static analysis in your process
Tools mentioned
- Code quality: PHP Mess Detector, PHP Copy/Paste Detector, PHP CodeSniffer, PHPStan, Psalm
- Dependencies: Composer Audit, Trivy
- Secrets: Trivy
- Security misconfiguration: Trivy, Iniscan
- Taint analysis: Semgrep, Psalm
Thank you
Get in touch to improve your PHP applications
- Free PHP cheat sheets: nth-root.nl/cheat-sheets
- PHP consulting services: nth-root.nl
- Personal website: nicwortel.nl
Attribution
- Slide theme based on github.com/julie-ng/tidy-revealjs
- Stock photos from pexels.com